Email - Hosting at home. Easy right..... right

Email - Hosting at home. Easy right….. right.
Next on my adventure of things I would like to self host, email. Email has been around for years, and so this is going to be a cake walk. Is what I said to myself nearly a week ago, and since then I have been on an interesting journey to say the least.
First up I needed to select a self hosting mail service. Now I could have gone properly off the deep end and installed postfix or dovecot, then gone looking for an opensource anti-virus program, anti-spam system then installed round cube for webmail, with all its dependencies, or and stay with me here, I could go looking for an opensource product to do all the heavy lifting for me.
Selecting a mail service.
So I threw the following (“open source mail server”) into google, and ended up on a Geek Flare article, talking about the “12 Best Self-Hosted email servers”. I spent some time clicking through the different options. I liked the look of Modoboa, but it seemed a little heavy weight, requiring Postgres or MySQL as the database backend. After poking around for a little while more I ended up on Poste.io. Which from the blurb on its home page happily quotes
SMTP + IMAP + POP3 + Antispam + Antivirus Web administration + Web email on your server in ~5 minutes”
We shall see about that.
DNS
As with everything on the internet, the first hurdle to deploying Poste, is DNS. Luckily the Poste website provides some useful guidance, but a little tweaking was required. We will come back to this later, but the long and short of it is you will need setup.
- PTR record
- The keen eye’d among you may already seen an issue here.
- A and CNAME records.
- I have setup a cname for mail.relf.co to point to my relf.co entry as thats where my mail server is hosted. With DDNS keeping the address updated.
- An MX record.
- Nice and easy.
relf.co MX mail.relf.co
- Nice and easy.
- DKIM
- We will spend some time here.
- SPF
- And here.
- DMARC
- And here.
Once DNS was setup it was onto
Installation.
The blurb wasn’t lying. It really did take me around 5 minutes to get the service installed and running. Following the instructions on the documentation page. I was able to get the docker image downloaded and running with very little effort. The only changes I made were to disable HTTPS (as I was going to use Caddy to be a reverse proxy for the web admin and webmail), changing the default HTTP port, and to set the time zone to “Europe/London”, oh I also had to add -d to the docker start command so that the container started detached, rather than running in foreground.
Once the containers were pulled, the service fired up and after setting a username and password for an admin user, I was presented with a lovely clean dashboard.
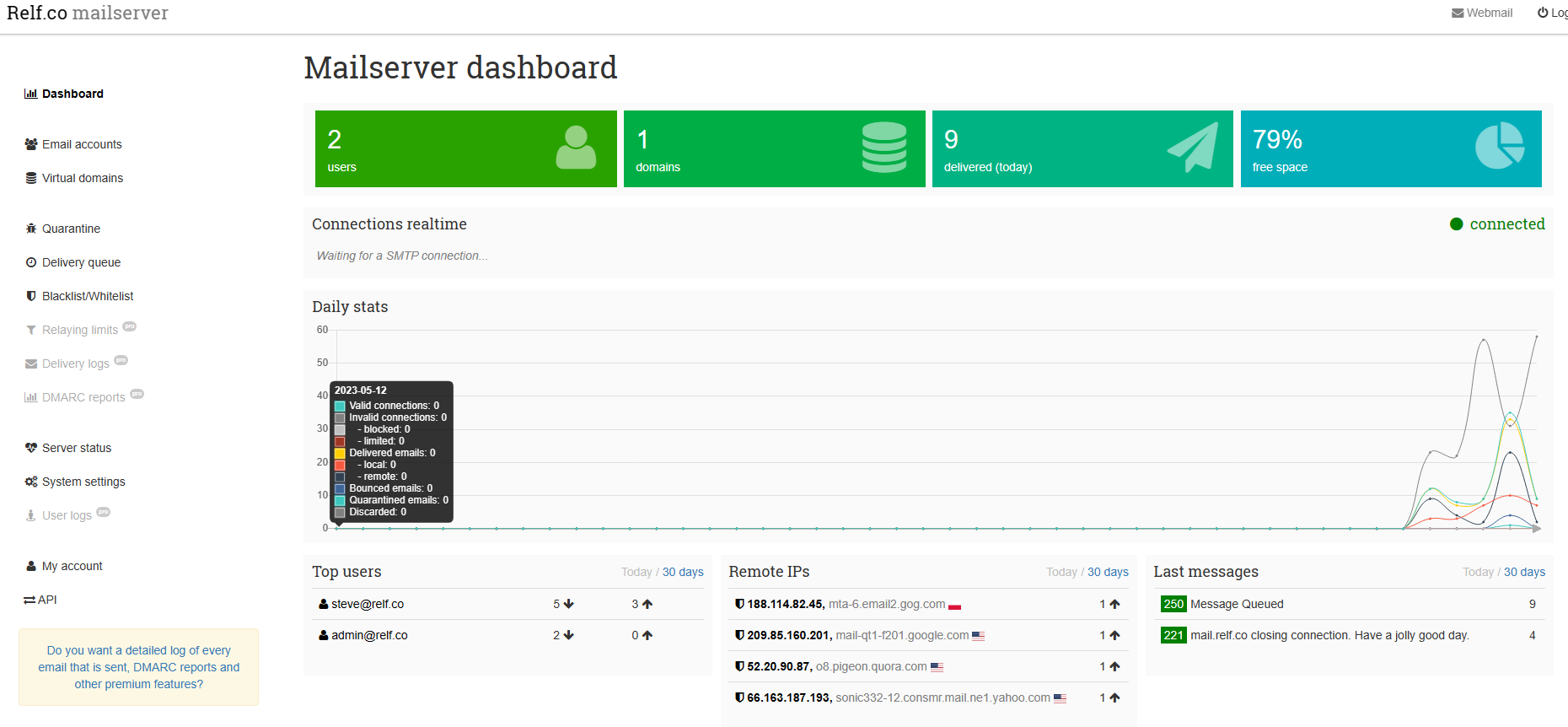
First time setup.
The first order of business was to pop into the “Server Status” page, on the left hand bar, and use the built in “Connection Diagnostics” button to ensure that all was right with our config. After adding a couple of extra ports to my port forwarding, everything was returning green, and it was off to the “Email Accounts” tab to create my email account. Again this was super easy. A simple case of entering a display name, and email address, and setting a password. Once complete, I was able to log into webmail, and start sending email.
DNS, DKIM, SPF, DMARC, Blocklists and Dynamic IP’s
If you have used an email service for more than 15 seconds you will have no doubt come across SPAM. Its a massive problem for email providers, somewhere in the region of 50% of all email traffic sent in 2022, which is down from 2014 where north of 60% of all email sent was spam. That is a crazy amount, of crap clogging up the tubes of the internet. So email providers have spent a long time, implementing multiple checks and balances to try and combat the amount of SPAM that can be delivered into a mail box.
The main items are SPF and DKIM.
Starting with SPF, SPF is a TXT type DNS record which a email receiving endpoint can query to ensure that the sending mail server is “allowed” to send email on behalf of the domain sending the email.
For example. I have a domain relf.co, and I want to send an email to someone at AOL.
My outgoing email connects to the AOL mail server and goes I have a email here for somene@aol.com, when the AOL mail server receives the message it will check the relf.co SPF record and check that the outgoing mail server is included in the record, if it is happy days, if its not, then depending on other factors, the email will either be bounced, sent to spam, or in rare cases delivered.
Next on the list of protections we have DKIM. DKIM, allows a sending mail server to sign outgoing email with a private key, then in DNS for the sending domain we the public part of the key. Then when a receiving mail server gets a signed incoming email, it looks up a specially formed DNS TXT record which contains the public key of the sending server, it uses this to then authenticate that the email has been sent from where it says it has.
Both SPF and DKIM are deemed secure, because in order to add the required TXT records you have to have access to the DNS server to make those updates.
One final piece of the puzzle is the DMARC. Domain-based Message Authentication, Reporting and Conformance (DMARC), allows domain owners to protect their domains from spoofing and other nasties, by telling receiving email servers how to respond to a verification failure of either DKIM or SPF.
DMARC allows three settings.
- Do nothing
- This does not guarantee the mail will be delivered, but the sender is not asking that these mails be dropped.
- Quarantine
- Asks the receiver to place the mail into spam or some other non inbox location.
- Reject
- Asks the receiver to outright reject any incoming mail that fails DMAC check.
Blocklists
Put simply a block list is a list of domains, and IP’s which have a bad reputation for spewing garbage onto the internet, and so these IP’s and domain names are added to blocklists that email operators subscribe to. If your on one of these blocklists, your ability to send email that is delivered is reduced significantly.
A long road to delivery.
I got most of the way there, I managed to get SPF, DKIM and DMARC to work mostly, but I was still having issues getting successful deliveries to AOL/Yahoo, and a couple of other places. Most of this related to having a dynamic IP address associated to my mail server. As its dynamic, I wasn’t able to set a PTR record for it, as that is manged by my ISP (if you have a static IP, you might well be able to self host). It then turns out that the entire subnet upon which my current dynamic IP sits, has been added to a block list. Which is basically game over. So at this point I was able to receive email into my private mail server, but not able to reliably send email, I needed a solution, and unfortunately this meant I was going to have to spend some money.
Dynu - Outgoing Mail Relay.
Luckily the folks over at Dynu offer a cheap but effective outbound mail relay, which is correctly configured with PTR records and all the other good stuff needed to ensure reliable delivery. I did have to make a couple of changes though.
- I had to set my mail server to relay through a smarthost.
- Again this was super easy inside the control panel.
- I had to remove my current DKIM keys and delete them from the mail server and from DNS
- I then had to create new DKIM keys and add them to DNS.
- I had to update my SPF TXT records to say that relay.dynu.com is allowed to relay for relf.co
It took me a little while to get everything squared away, but I am now please to announce, I have a mostly self hosted email setup. If I could get a static home IP, I could do without the Dynu outgoing relay.
Overall this has been an interesting little side project, and I am mostly happy with the outcome, it does now mean I am in the position of being able to cancel my external web hosting.
Until next time, Steve.